Vibe Coding Security: 7 Critical Practices You Can't Skip in Vibe Coding
Master the essentials of coding security with these 7 critical practices every developer must follow to protect your code
In the fast-paced world of software development, it's easy to get caught up in features, functionality, and deadlines. But what often takes a back seat, sometimes with catastrophic consequences, is security. Even the most elegant code can become a gaping vulnerability if fundamental security practices are ignored.
Whether you're a seasoned pro or just starting your coding journey, understanding and implementing these seven essential security practices is non-negotiable. They are the bedrock of secure applications, safeguarding your data, your users, and your reputation.
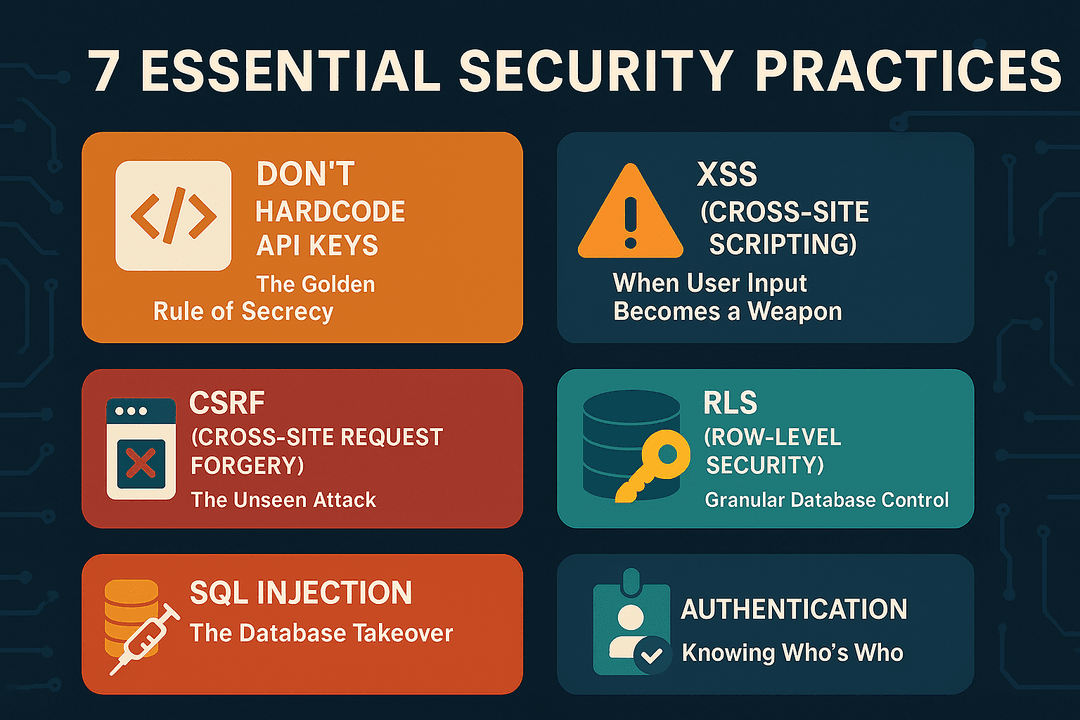
1. Don't Hardcode API Keys: The Golden Rule of Secrecy
This is arguably the most fundamental security tenet. Never embed API keys, database credentials, or any other sensitive secrets directly into your source code.
Why it matters: Your code, especially if it's pushed to a public repository (even a private one can be leaked), is a potential treasure trove for attackers. If your keys are hardcoded, a single leak instantly exposes them, giving malicious actors direct access to your services, databases, or third-party accounts.
The Solution: Utilize environment variables. Store your keys in an .env file (which should be excluded from version control using a .gitignore file) and load them programmatically into your application. This ensures your secrets remain separate from your codebase, even if the code itself is compromised.
2. XSS (Cross-Site Scripting): When User Input Becomes a Weapon
XSS is a common and dangerous web vulnerability where attackers inject malicious client-side scripts (usually JavaScript) into web pages viewed by other users. This can lead to session hijacking, data theft, or even defacement of your website.
Why it matters: If your application renders unvalidated user input directly into HTML, you're creating an open door for XSS. Imagine a comment section where a user posts <script>alert('You've been hacked!');</script>. If unescaped, every user viewing that comment will execute that script.
The Solutions:
- Escape Output: This is your primary defense. Always treat user input as plain text, not code. Before displaying any user-generated content, escape special characters (like
<,>,&,",') so they are rendered literally, not interpreted as HTML or script. - Sanitize Input: Go a step further by cleaning and validating user input on the server-side before storing or displaying it. This might involve removing unwanted tags, attributes, or ensuring data conforms to expected formats.
- Content Security Policy (CSP): Implement a robust CSP to define which sources of content are allowed to be loaded and executed on your web pages. This acts as an additional layer of defense, blocking unauthorized scripts even if an XSS vulnerability exists.
3. CSRF (Cross-Site Request Forgery): The Unseen Attack
CSRF tricks a user's browser into executing an unwanted action on a web application where they are currently authenticated. The user is unaware of the attack, and the request appears legitimate to the target application because it carries the user's session cookies.
Why it matters: An attacker could craft a malicious website that, when visited by your logged-in user, silently sends a request to your application to, say, change their email, transfer funds, or delete an account.
The Solution:
- CSRF Tokens: The most common and effective defense is to generate a unique, cryptographically secure CSRF token for each user session. This token is embedded in all forms and AJAX requests. Your server then validates this token upon receiving a request. If the token is missing or invalid, the request is rejected. This ensures that only requests originating from your legitimate application (which knows the token) are processed.
4. RLS (Row-Level Security): Granular Database Control
When working with databases, especially relational ones like Postgres, managing data access at a granular level is crucial. Row-Level Security allows you to restrict which rows a user can access or modify based on their roles or other attributes, directly within the database.
Why it matters: Without RLS, if an attacker gains access to your application, they might be able to query the entire database, exposing data they shouldn't see. RLS helps enforce the principle of least privilege directly at the data layer.
The Solution: Learn and implement your database's RLS capabilities. For example, in Postgres, you can define policies that dictate which rows are visible or modifiable by specific users or roles, ensuring that users only interact with the data they are authorized to see.
5. SQL Injection: The Database Takeover
SQL injection occurs when attackers manipulate database queries by injecting malicious SQL code through user input fields. This can allow them to bypass authentication, access sensitive data, modify data, or even gain control of your database server.
Why it matters: If you construct SQL queries by directly concatenating user input, you're setting yourself up for disaster. An input like ' OR '1'='1 in a login field could bypass authentication entirely.
The Solution:
- Prepared Statements / Parameterized Queries: This is your strongest defense. Always treat user input as data, not code. Prepared statements separate the SQL command from the data. The database then understands that the user input is a value to be inserted into a placeholder, not an executable part of the query. This prevents malicious SQL from altering the query's intent.
6. Authentication: Knowing Who's Who
Authentication is the process of verifying a user's identity. A strong authentication system is the first line of defense against unauthorized access.
Why it matters: Weak or improperly implemented authentication mechanisms can allow attackers to easily gain access to user accounts or privileged areas of your application.
The Basics to Master:
- Sessions: Server-side mechanisms to maintain user state over multiple requests, often tied to a unique session ID stored in a cookie.
- Cookies: Small pieces of data stored by the browser, commonly used to hold session IDs. Understand
HttpOnlyandSecureflags for cookie security. - JWTs (JSON Web Tokens): A compact, URL-safe means of representing claims to be transferred between two parties. Often used for stateless authentication in APIs. Learn about signing, verification, and token expiration.
- Secure Logins: Implement secure password hashing (never store plain text passwords!), rate limiting on login attempts, and multi-factor authentication (MFA) whenever possible.
7. Server-Side vs. Client-Side: Understanding the Divide
This fundamental distinction is crucial for securing your application logic and data.
- Client-Side: Code that runs in the user's web browser (e.g., JavaScript, HTML, CSS). It is fully visible and manipulable by the user.
- Server-Side: Code that runs on your web server (e.g., Node.js, Python, Ruby, PHP). It is hidden from the user.
Why it matters: Any sensitive logic or secrets placed on the client-side are inherently insecure. An attacker can easily inspect, modify, or bypass client-side code.
The Rule: Never trust the client. Always perform critical operations, validation, and data handling on the server-side. Authentication checks, authorization logic, database queries, and sensitive business rules must reside on the server. The client-side should only be responsible for user interface and making requests to the server.
Conclusion
Security isn't an afterthought; it's an integral part of the development process. By diligently applying these seven core practices – from safeguarding your secrets to validating every input and understanding the server-client boundary – you'll build more robust, resilient applications and contribute to a safer digital world. Make these practices part of your development "vibe" from day one!